Slide 1 - Security Assurance Efforts 2025
This title slide, titled "Security Assurance Efforts 2025," presents an overview of Security Assurance Efforts for 2025. The subtitle highlights "Managing Customer Requests by Depth of Assurance."
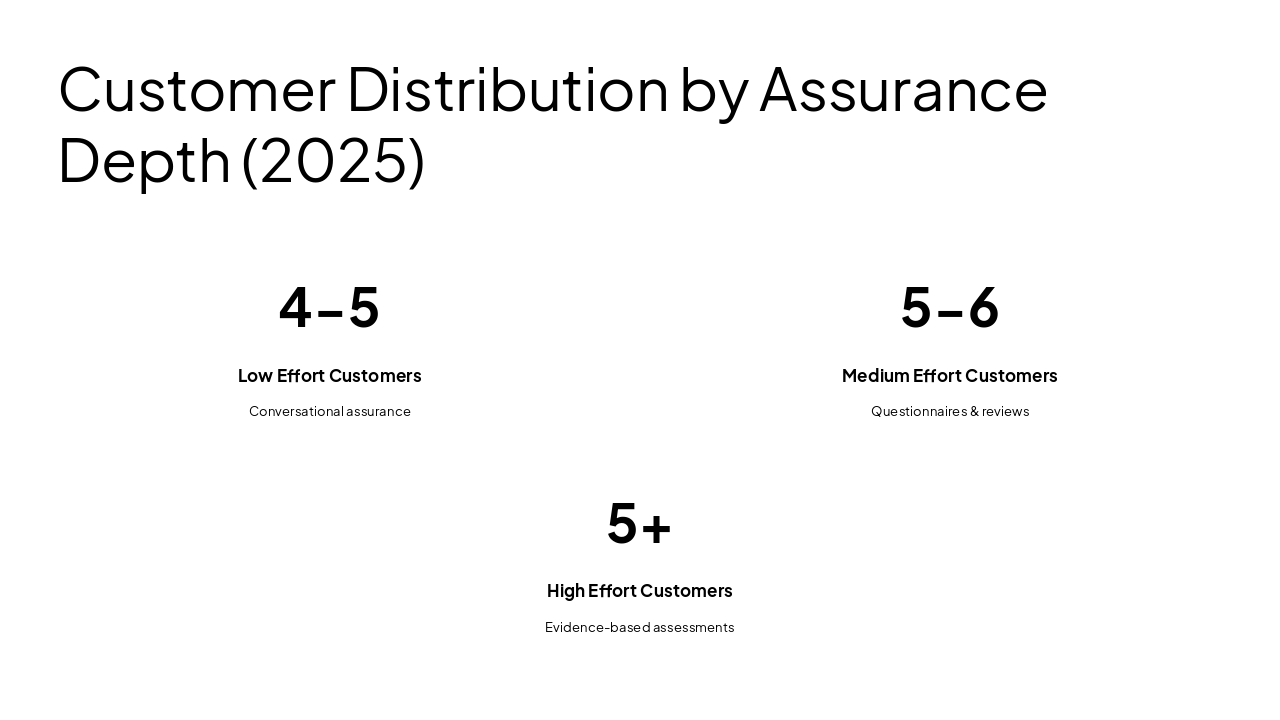
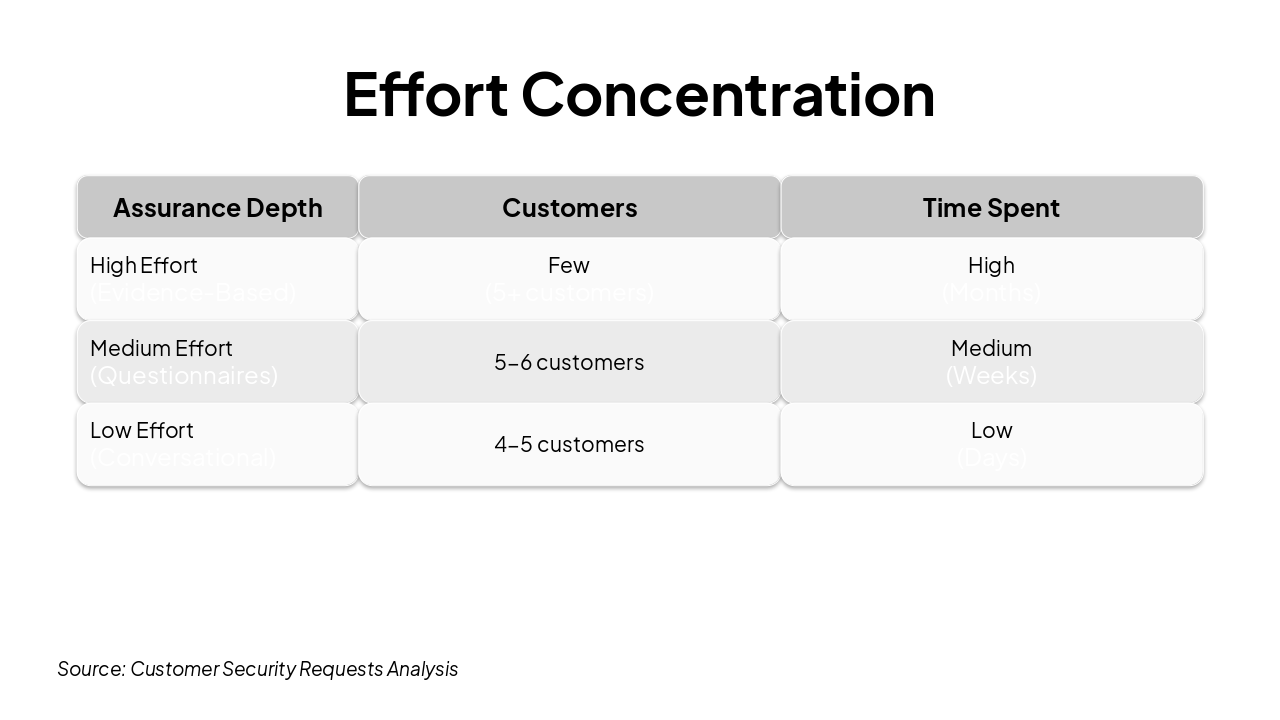
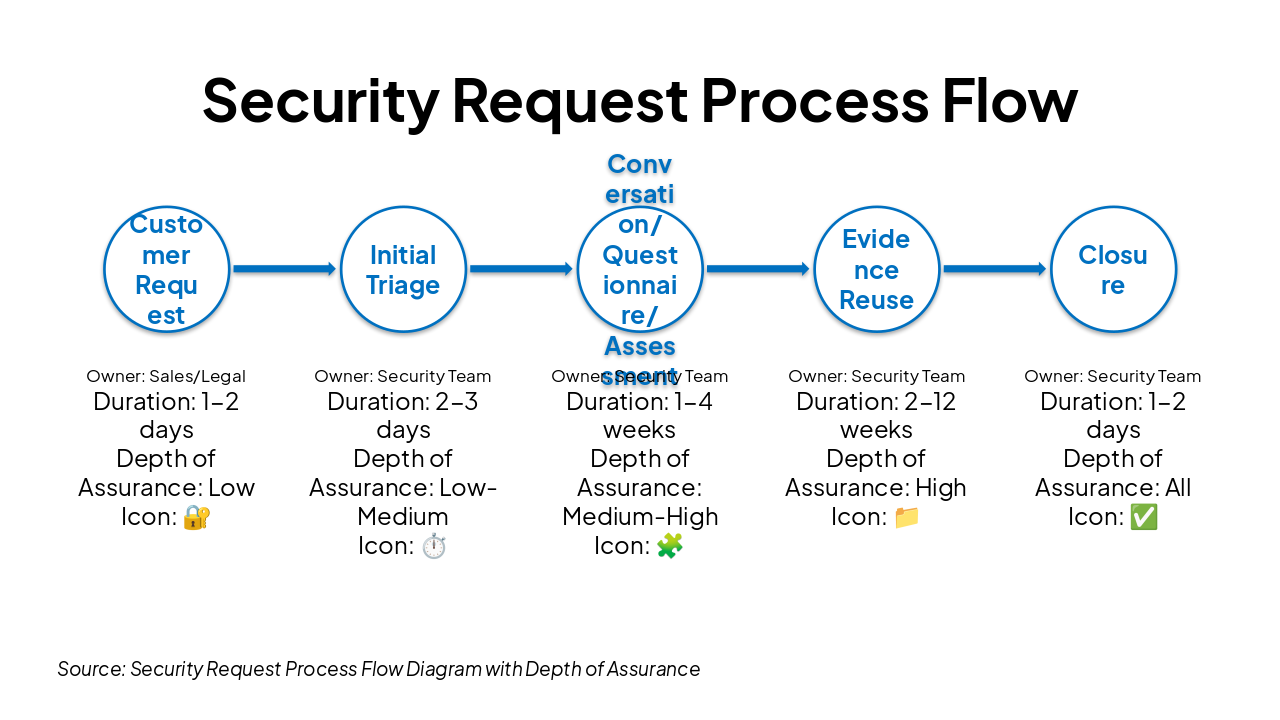
Security Assurance Efforts Overview 2025
Managing Customer Requests by Depth of Assurance
Source: Welcome slide introducing management of customer security requests by depth of assurance