Slide 1 - 2026 Security Roadmap
This title slide is headed "2026 Security Roadmap." Its subtitle emphasizes "Enabling Business Growth Through Strategic Security."
2026 Security Roadmap
Enabling Business Growth Through Strategic Security

Generated from prompt:
Create a GM/CEO-level PowerPoint presentation titled '2026 Security Roadmap' for a mid-to-large enterprise with a 25-person security organization. The presentation should be executive, business-focused, and position security as a business enabler. Include the following mandatory slides: 1. Executive Summary – key outcomes, business value, and risk reduction. 2. Why Now? – business risk perspective (cyber, regulatory, reputational). 3. Current State – high-level maturity and limitations. 4. 2026 Security Vision – clear vision and strategic principles (Zero Trust, automation, risk-based). 5. Security Organization Evolution – 'Today vs 2026' comparison. 6. Target Security Organization Model – service domains: Managed Detection & Response, Identity & Privileged Access Services, Endpoint & Workload Protection, Data Security Services, Adversary Simulation & Assurance. 7. From Tools to Capabilities – how technologies evolve into capabilities. 8. 2026 Flagship Security Initiatives – 5–7 major initiatives with purpose, value, and risk reduction. 9. Security Team Evolution – 25-person structure transformation, specialization, automation. 10. Security Trends We Align With – Zero Trust, XDR, AI-assisted SOC, continuous validation, data-centric security. 11. Roadmap Timeline – quarterly Q1–Q4 2026. 12. Success Metrics & KPIs – risk-based metrics (MTTD, MTTR, automation rate, etc.). 13. Investment Overview & Value – investment categories, expected returns. 14. Risks & Management Expectations – dependencies, leadership support. 15. Closing Message – security as a strategic business capability. Include short speaker notes per slide for presentation delivery. Avoid tool/vendor focus. Emphasize clarity, persuasion, and business alignment.
Executive PPT for GM/CEO outlining 2026 security evolution: 40% risk reduction, Zero Trust vision, org transformation from 25-person team, flagship initiatives, timeline, KPIs, investments. Positions
This title slide is headed "2026 Security Roadmap." Its subtitle emphasizes "Enabling Business Growth Through Strategic Security."
Enabling Business Growth Through Strategic Security

The Executive Summary slide outlines key benefits, including a 40% enterprise risk reduction and unlocking $XM in business value. It also highlights achieving Zero Trust maturity, deploying automated operations, and enabling faster secure innovation.
Source: 2026 Security Roadmap

The "Why Now?" slide highlights escalating cyber threats, including a 50% YoY rise in ransomware attacks that cripple operations and hit revenue. It also warns of record-high GDPR fines totaling billions and reputational breaches driving customer churn and market share loss, demanding urgent action.
| Escalating Cyber Threats | Regulatory & Reputational Risks |
|---|---|
| Ransomware attacks up 50% YoY, crippling operations and extracting multimillion ransoms. Cyber adversaries evolve faster, directly hitting revenue and continuity. | GDPR fines hit record highs, totaling billions. Reputational breaches erode customer trust, driving churn and lost market share. Urgent action demanded. |
Source: 2026 Security Roadmap

The "Current State" slide shows a 72-hour MTTR indicating reactive maturity and 60% coverage gaps from siloed tools. It also highlights high manual processes limited by skill shortages and a strained team of 25 FTEs.
Reactive maturity level
Siloed tools exposure
Skill shortages limit
FTEs strained by gaps

The 2026 Security Vision slide outlines a proactive, automated, risk-based defense with Zero Trust architecture implemented everywhere. It also highlights AI-driven security operations and fully integrated services.

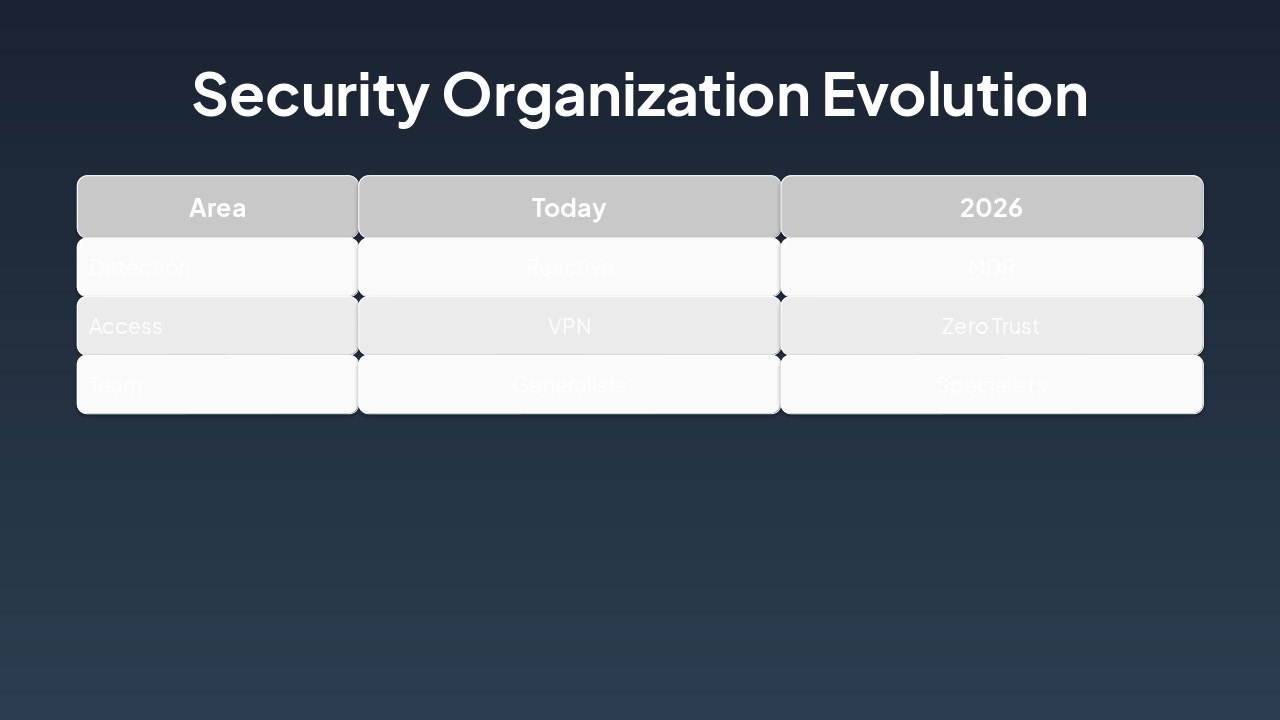
The slide "Security Organization Evolution" compares current security practices to planned 2026 advancements in a table. It highlights shifts from reactive detection/VPN/generalists today to MDR/Zero Trust/specialists by 2026.
{ "headers": [ "Area", "Today", "2026" ], "rows": [ [ "Detection", "Reactive", "MDR" ], [ "Access", "VPN", "Zero Trust" ], [ "Team", "Generalists", "Specialists" ] ] }
The "Target Security Organization Model" slide presents a feature grid of five key security services. These include managed detection & response for threat hunting, identity & privileged access controls, endpoint & workload protection, data security, and adversary simulation for resilience testing.
{ "features": [ { "icon": "🔍", "heading": "Managed Detection & Response", "description": "Proactive threat hunting and rapid response to minimize breach impact." }, { "icon": "🔐", "heading": "Identity & Privileged Access", "description": "Secure access controls to protect critical credentials and reduce insider risks." }, { "icon": "🛡️", "heading": "Endpoint & Workload Protection", "description": "Advanced defenses for devices and cloud workloads against evolving attacks." }, { "icon": "🔒", "heading": "Data Security Services", "description": "Comprehensive protection for sensitive data across storage and transit." }, { "icon": "🎯", "heading": "Adversary Simulation & Assurance", "description": "Continuous testing and validation to ensure resilience against real threats." } ] }

The slide outlines a security workflow progression from "Tools" (deploying point solutions like SIEM for siloed detection) to "Integration" (unifying into platforms like XDR for holistic visibility and efficiency). It advances through "Processes" (embedding automation for streamlined operations) to "Capabilities" (enabling functions like threat hunting for proactive risk reduction and resilience).
{ "headers": [ "Stage", "Key Activities", "Outcome" ], "rows": [ [ "Tools", "Deploy point solutions (e.g., SIEM)", "Tactical, siloed detection" ], [ "Integration", "Unify into platforms (e.g., SIEM → XDR)", "Holistic visibility & efficiency" ], [ "Processes", "Embed automation & workflows", "Streamlined operations" ], [ "Capabilities", "Enable advanced functions (e.g., Threat Hunting)", "Proactive risk reduction & business resilience" ] ] }
Source: 2026 Security Roadmap - Slide 7

This agenda slide outlines six flagship security initiatives for 2026, including Zero Trust Rollout, AI-Powered SOC, XDR Platform Deployment, Data-Centric Security, Adversary Simulation Program, and Identity & Access Evolution. Each highlights key benefits like reducing breach risks by up to 90%, cutting threat response times by 60%, and improving detection across environments.
Implement zero trust model; reduces breach risk 50% by eliminating implicit trust.
Deploy AI-driven SOC; cuts MTTR 60% for faster threat response.
Unified extended detection/response; improves MTTD 40% across environments.
Protect data everywhere; reduces breach impact 70% with encryption and DLP.
Continuous red teaming; uncovers 80% more vulnerabilities proactively.
Advanced IAM/PAM services; prevents 90% privilege abuse incidents. Source: 2026 Security Roadmap

Today, a 25-person team of generalists handles broad security duties, causing inefficiencies, slower MTTR, and scalability limits. By 2026, the same team shifts to specialists (8 MDR, 6 EPP, plus others) with 40% automation for routine tasks, enabling focus on high-value work and superior outcomes.
| Today | 2026 |
|---|---|
| 25 generalists handle broad security duties across detection, response, and protection. Lacks specialization, leading to inefficiencies, slower MTTR, and scalability limits. | Specialized experts: 8 MDR, 6 EPP, plus others. 40% automation handles routine tasks. Same 25-person team focused on high-value work for superior outcomes. |

This slide lists key security trends we align with, such as embracing Zero Trust Architecture and implementing Extended Detection & Response (XDR). It also covers leveraging AI-assisted SOC, enabling continuous threat validation, prioritizing data-centric security, and adopting a business-aligned strategy.

The Roadmap Timeline outlines a 2026 security maturity plan across four quarters. It begins with vision and organization design in Q1, advances to Zero Trust pilot in Q2 and MDR deployment in Q3, and culminates in full operations with KPIs in Q4.
Q1 2026: Vision and Org Design Define security vision, evolve organization structure for 2026 maturity. Q2 2026: Zero Trust Pilot Launch Zero Trust pilot across key business units for validation. Q3 2026: MDR Deployment Deploy Managed Detection & Response for enhanced threat visibility. Q4 2026: Full Operations + Metrics Achieve full operations with established KPIs and continuous metrics.
Source: 2026 Security Roadmap

The slide presents key success metrics and KPIs, with MTTD reduced to under 4 hours from a 24-hour baseline and MTTR under 12 hours. It also shows a 50% automation rate, 95% coverage, and a 30% reduction in risk score.
from 24h baseline

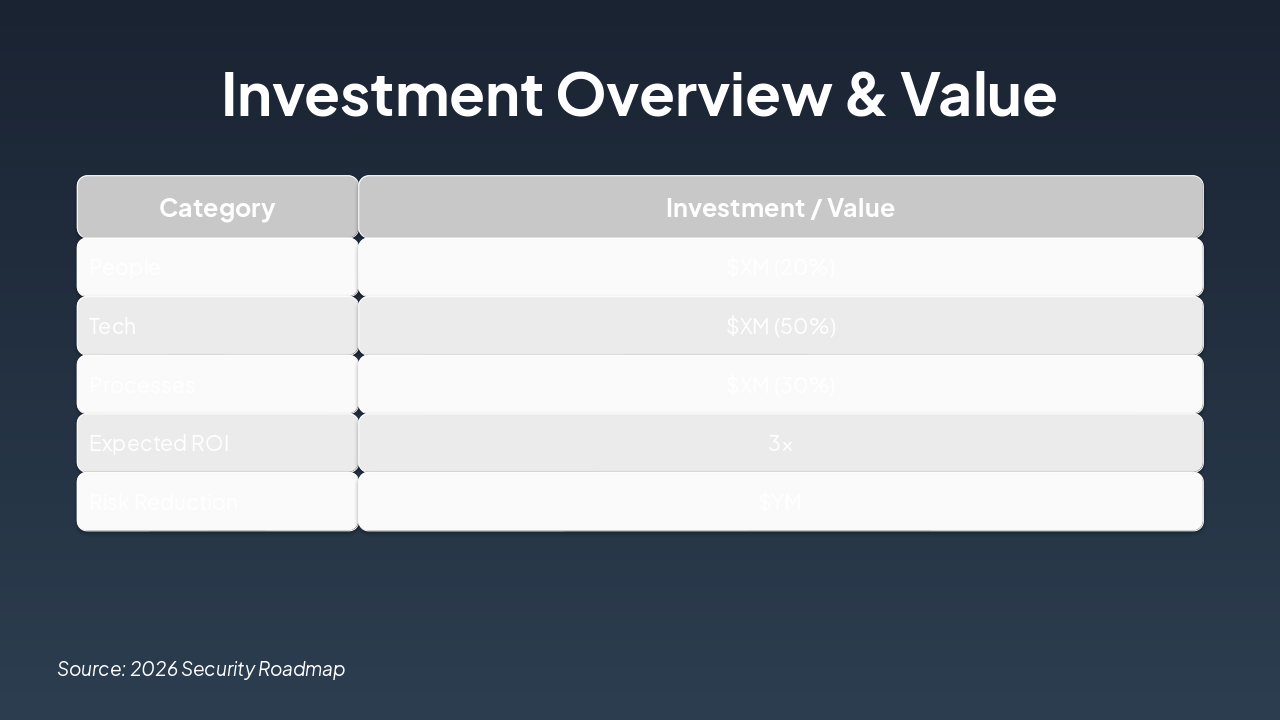
The slide provides an investment overview totaling $XM, allocated as 20% to People, 50% to Tech, and 30% to Processes. It projects a 3x expected ROI and $YM in risk reduction.
{ "headers": [ "Category", "Investment / Value" ], "rows": [ [ "People", "$XM (20%)" ], [ "Tech", "$XM (50%)" ], [ "Processes", "$XM (30%)" ], [ "Expected ROI", "3x" ], [ "Risk Reduction", "$YM" ] ] }
Source: 2026 Security Roadmap
The slide identifies key risks like adoption delays and skills gaps, with mitigations via training programs and executive support. It outlines expectations for leadership buy-in and sustained funding, stressing proactive management for roadmap success.
Source: 2026 Security Roadmap

This conclusion slide, titled "Closing Message," positions security as a strategic business capability that enables innovation and protects growth. It includes a subtitle calling to "Approve Roadmap."
Security as Strategic Business Capability Enables Innovation, Protects Growth
Approve Roadmap
Source: 2026 Security Roadmap

Explore thousands of AI-generated presentations for inspiration
Generate professional presentations in seconds with Karaf's AI. Customize this presentation or start from scratch.